Enabling two factor authentication for GitLab with a MIRkey security key
From a security perspective, using a security key rather than a TOTP code generated by an Authenticator App (aka “2FA”) is a step up. While a TOTP code may be intercepted as part of a phishing attack, this is not possible with a security key
In this how-to we will show you how to enable the MIRkey security key as a second factor for GitLab.
Note that currently (v11.6) GitLab requires 2FA to be set up before allowing a security key to be registered. You can follow these instructions to use a MIRkey for 2FA or use an authenticator app.
However, using a security key is a better user experience - just plugin the key and press the button when prompted - and it is more secure.
-
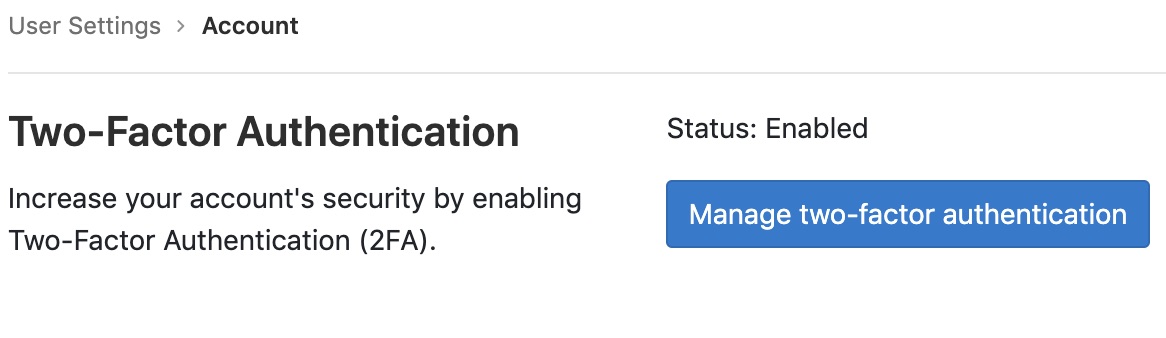
Open your Gitlab account settings (your domain/profile/account), and click on “Manage two-factor authentication”.
-
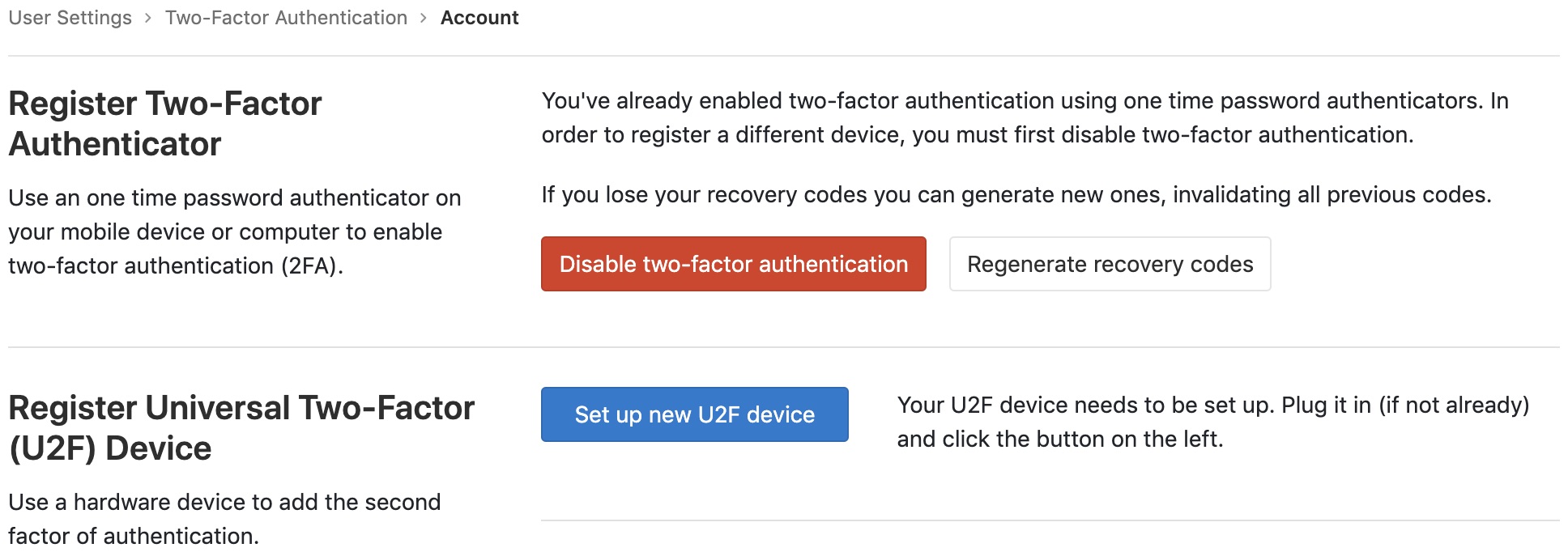
Plug in your MIRkey, press the button, and then click “Set up new U2F device”
-
Select a name to uniquely identify the key - we recommend you use the last 2 digits of the serial number printed on the device.
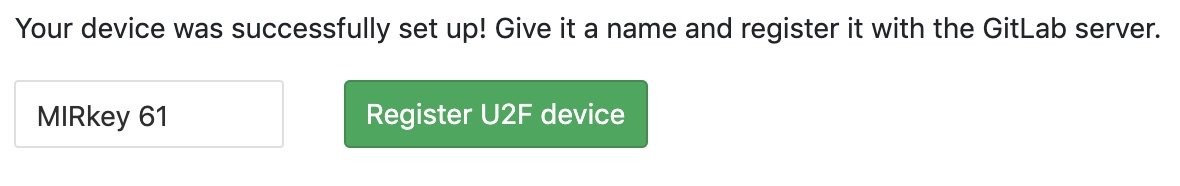
Click “Register U2F device”. Your key is now registered.