Microsoft Authenticode Code signing with the eHSM Hardware Security Module
When you purchase a code signing certificate from Thawte, they issue this advisory:
PRIVATE KEY PROTECTION ADVISORY: To protect your business and reduce the risk of stolen, misplaced, or compromised Code Signing private keys, Thawte strongly advocates stringent adherence to private key management best practices. To learn more about Code Signing private key protection best practices, visit: https://search.thawte.com/support/ssl-digital-certificates/index?page=content&id=INFO2947
This how-to will guide you to secure your code signing key and sign executables with the eHSM
Note: using the eHSM network daemon will help you to centralize your keys and should form part of your key management strategy.
Prerequisites:
If you have not done so already, install the eHSM KSP (Key Storage Provider) for Microsoft CNG and the eHSM Manager. Both are available on the downloads page.
Ideally you should generate the signing key pair on the HSM so it never leaves the confines of the security module, but if you have not done so, this how-to also helps you to import an existing key and certificate.
-
If your code signing certificate is currently in a .pfx file, you will need to split it into a key and certificate:
certutil -split -dump keyandcert.pfxOr using openssl:
openssl pkcs12 -in keyandcert.pfx -nocerts -out key.pem openssl pkcs12 -in keyandcert.pfx -clcerts -nokeys -out certificate.crt -
Import the key into the HSM using the eHSM Manager (Tools -> Import a private key…)
Ensure that you use a unique label and ID for the key.
-
Import the certificate into the windows certificate store:
Note: If you already have the certificate installed with the software key, you will first need to delete it.
This how-to uses the Personal or “MY” store, but you can also import it into the machine keystore for use from scripts running as a system user. In this case, remove the “-user” option in the steps below. You will then be required follow these instructions in an admin command prompt.
Open the certificate manager and right click on the Certificates item under “Personal”.
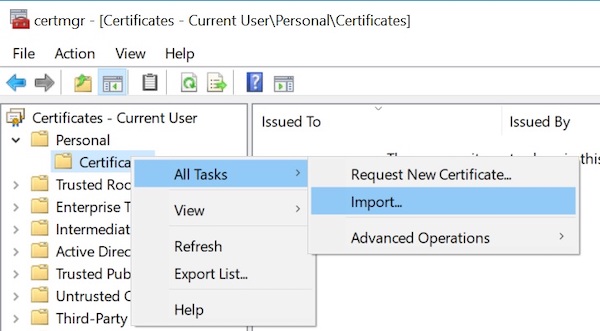
Select the certificate.crt file you created in step 1 and follow the instructions:
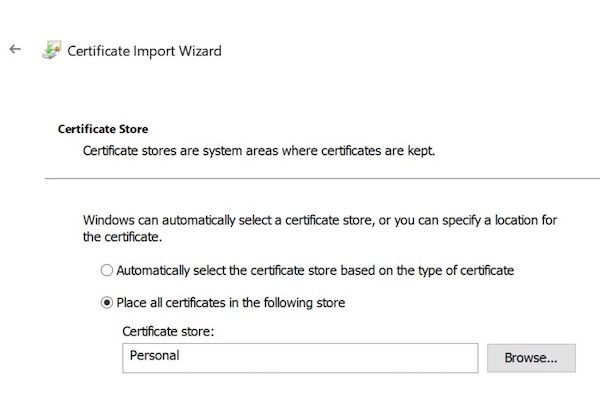
-
Associate the certificate with the key in the HSM:
Retrieve the thumbprint of the certificate (copy the “sha1 hash” from the output below)
certutil -user -store myThis command will associate the certificate with the key in the HSM:
certutil -user -csp "eHSM Key Storage Provider" -repairstore My "hash"My "Personal" ================ Certificate 0 ================ Serial Number: 1928a70a9e53d24e1154de786b0c60c5 Issuer: CN=thawte SHA256 Code Signing CA, O=thawte, Inc., C=US NotBefore: 2018/11/21 2:00 AM NotAfter: 2019/11/22 1:59 AM Subject: CN=ACME, O=ACME Co, L=Huntsville, C=US Non-root Certificate Cert Hash(sha1): 51a96f0317258485701182b8a5db6cf163e1ae02 Key Container = codesign Provider = eHSM Key Storage Provider Private key is NOT exportable Encryption test passed CertUtil: -repairstore command completed successfully.During the association you will be asked for the HSM user password:
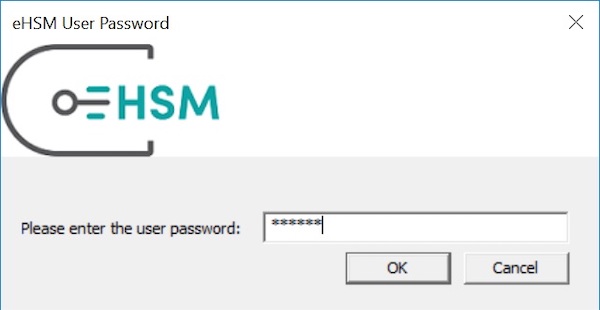
-
Now you can use signtool as follows:
signtool sign /tr http://timestamp.digicert.com /td sha256 /fd sha256 /sha1 51a96f0317258485701182b8a5db6cf163e1ae02For unattended signing and use of the KSP (also in Active Directory), you can set following environment variable before using signtool:
set ehsm_pin="hsm user password" -
Remove all traces of the file based private key (.pfx file).