Configuring OpenSSH to use the eHSM Hardware Security Module or MIRkey
Last updated 2019-04-12
You can setup SSH to use an eHSM or MIRkey using either the eHSM Manager or a standard PKCS#11 command-line tool like p11tool.
Using the eHSM Manager
Download the eHSM Manager for your platform here.
-
From the Tools menu, select “Generate RSA Key Pair”:
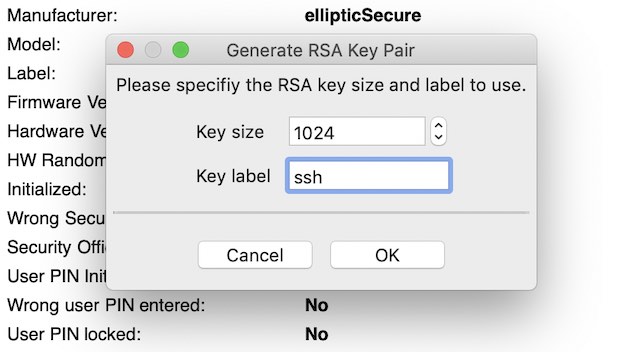
-
After the key is created, save the public key PEM file as “ssh.pem”, then convert the .pem file to OpenSSH format:
ssh-keygen -f ssh.pem -i -mPKCS8 -
Copy this key to the remote server authorized_keys file (or use ssh-copy-id)
-
Now you can Login with the key stored on the eHSM, OpenSSH will automatically match the key on the server with the key in the eHSM:
ssh -I /usr/local/lib/libehsm.dylib user@example.com
Using the commandline p11tool
If your platform supports the p11tool, you can use it to accomplish the same task (with a bit more typing).
-
Listing the available tokens:
p11tool --provider=/usr/local/lib/libehsm.dylib --list-tokens -
Use the URL from the command above to generate a key pair on the eHSM:
p11tool --provider=/usr/local/lib/libehsm.dylib --login "url" --generate-rsa --outfile="ssh.pem"\ --label="ssh" --bits 2048 -
Optionally list the generated key pairs:
p11tool --provider=/usr/local/lib/libehsm.dylib --login "url" --list-all -
Check if ssh can see the public key:
ssh-keygen -D /usr/local/lib/libehsm.dylib ssh-rsa "key output in base 64" -
Follow steps 3-4 from above.